Automate Postman Secret Scanning With Trufflehog
Introduction
Unintentional secret exposure on the internet is a problem as old as the internet itself. While hunter2 may not have been the first password to be inadvertently shared for everyone to see, it has certainly not been the last. Since then, a significant number of new websites and tools have been released that make it even easier to accidentally disclose credentials, including passwords, private keys, API keys, and more. Some websites, such as Pastebin and its various clones, have been maliciously used to publish dumps of this information. Others, like GitHub are taking active steps to detect and alert on these credentials to prevent their misuse. Lately, I have been working with a team that has been researching scanning for secrets in Postman.
Common Sources of Secrets in Postman
Postman offers a number of ways to manage data used in making API calls. Some of this is protected, but much of it is not. The most common sources of credentials are the request headers and environment variables. However, credentials can easily be found in a number of other places as well.
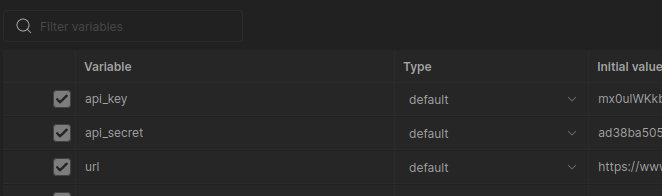
Environment Variables
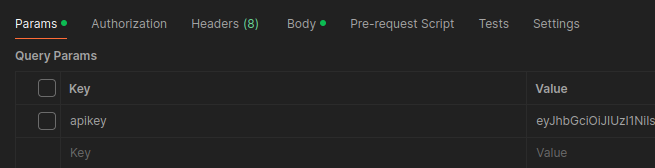
Params
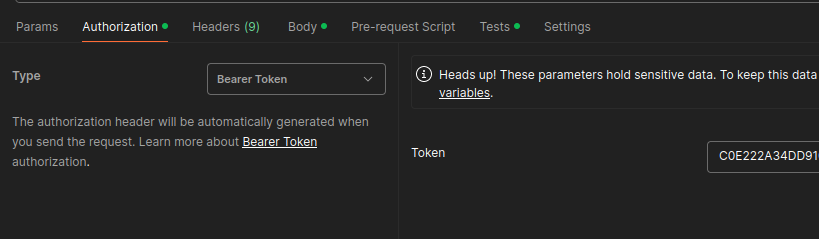
Authorization
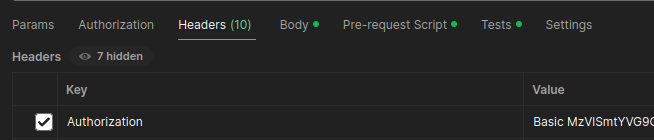
Headers
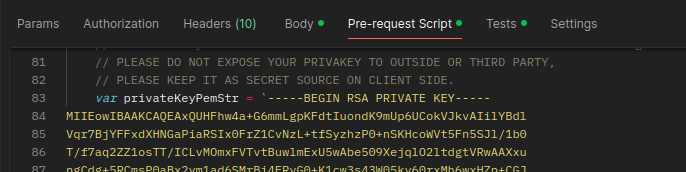
Params
Starting the Automation Process
However, there is an easier way to programatically retrieve this information: using the Postman API. If you know the GUID of your target request, you can get the JSON data directly without an API key.
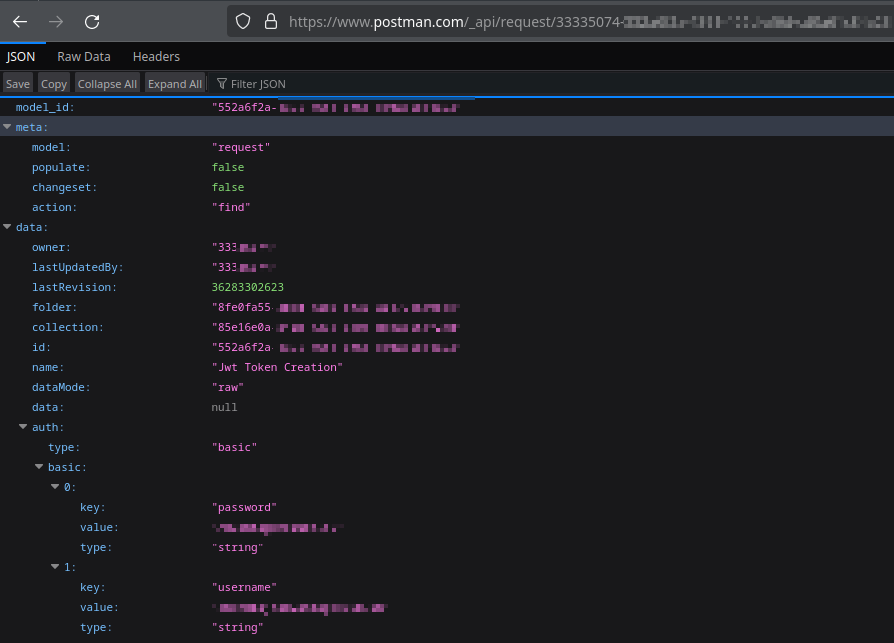
Postman API
This means that we can start with a file including a list of unique URLs found on the Postman network and filter to only the ones that contain request IDs:
cat unique_urls.json |jq -r .[] > urls
grep "/request/" urls > requestsThen we can modify those URLs to use the Postman API syntax:
Postman API Request URLs
Fetch all of these URLs using your favorite tool, save them locally, and now you can use Trufflehog to scan for secrets in these request files.
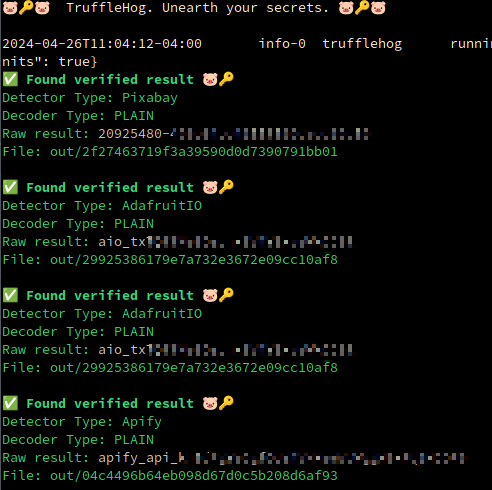
Verified Secrets
This workflow is great, but we can go a step further and automate the process of fetching request IDs.
Automating the Search
There are two ways to automate the search on Postman; however, it is worth noting that both methods are limited to 200 (ish) results. This means that more specific search terms will provide better results with a smaller number of requests hidden by this cap.
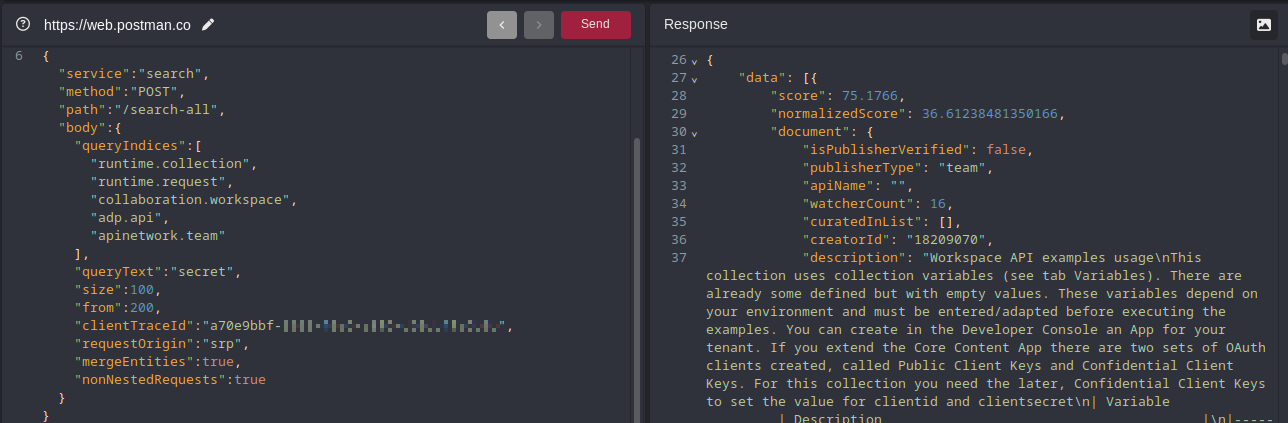
Method 1: Websockets (POST https://web.postman.co/_api/ws/proxy)
Using the Postman websockets API allows for a machine-friendly way to automatically gather data. This works well as long as Postman supports it and allows it to be used.
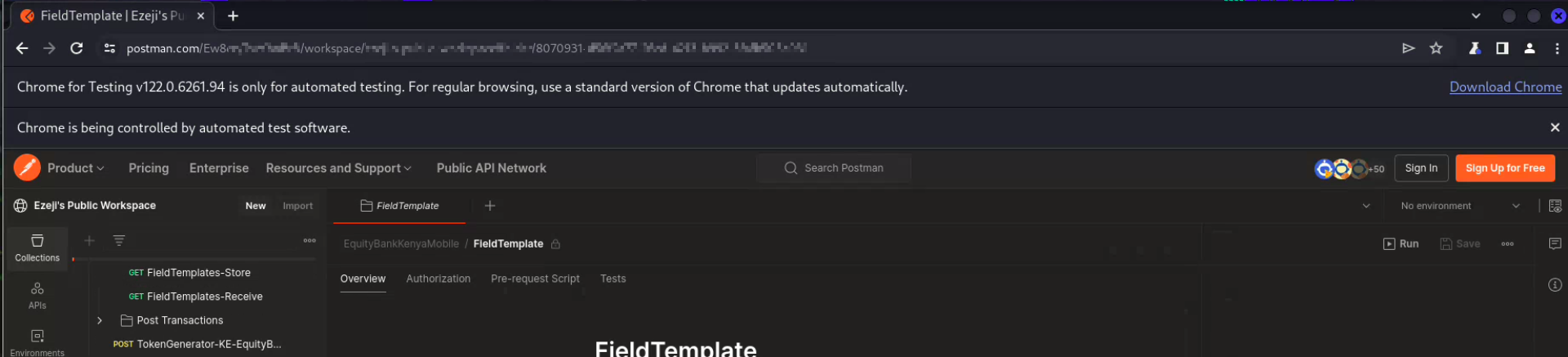
Method 2: Selenium
If (or when) the Postman websockets API becomes inaccessible for any reason, you can use Selenium or other browser automation tools that are typically used for integration testing to navigate the Postman website for you and extract relevant data.
Optimizing the Search
In order to maximize the signal-to-noise ratio in a search in an attempt to stay below the results cap where possible, our team has created a tool that fetches domains that are in-scope for bug bounty programs: devcoinfet/postman_research.
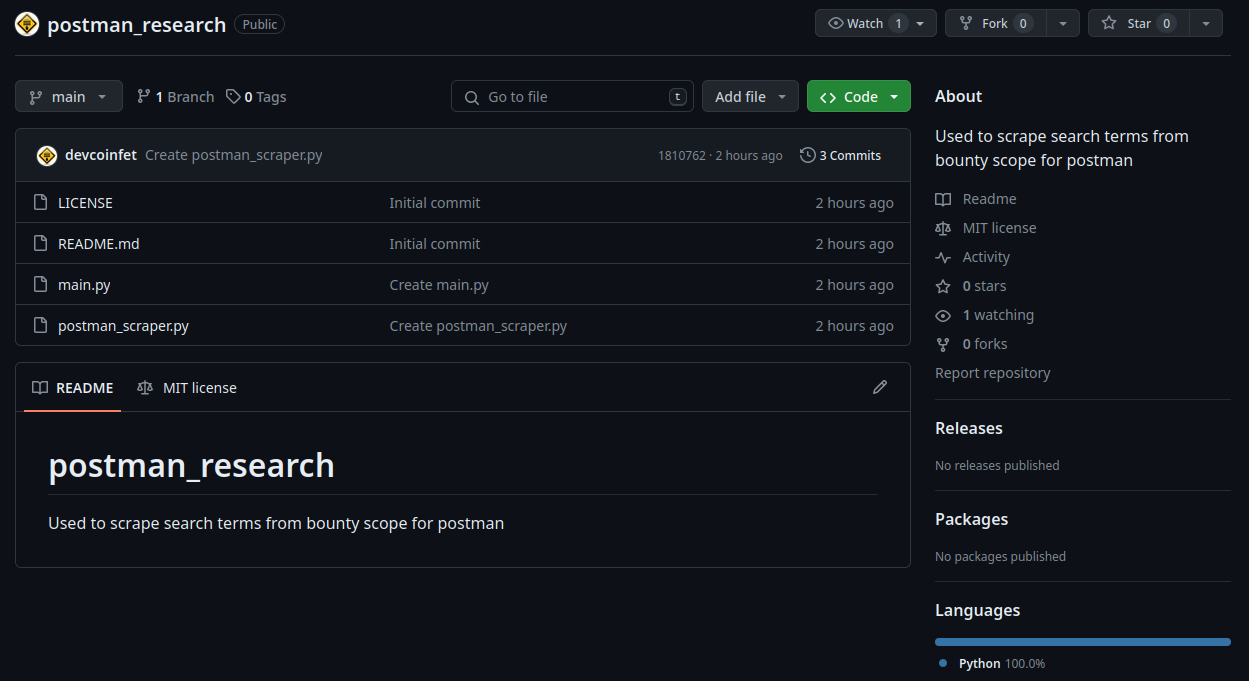
Postman scraping and parsing tooling
This still has room for improvement in terms of reducing noise further; however, the tooling has already resulted in a number of reported findings.
Coming Soon: Even More Automation
Recently, Truffle Security released a post on this subject (Postman Carries Lots of Secrets) that details an additional tool we can use: using trufflehog to directly search target workspaces.
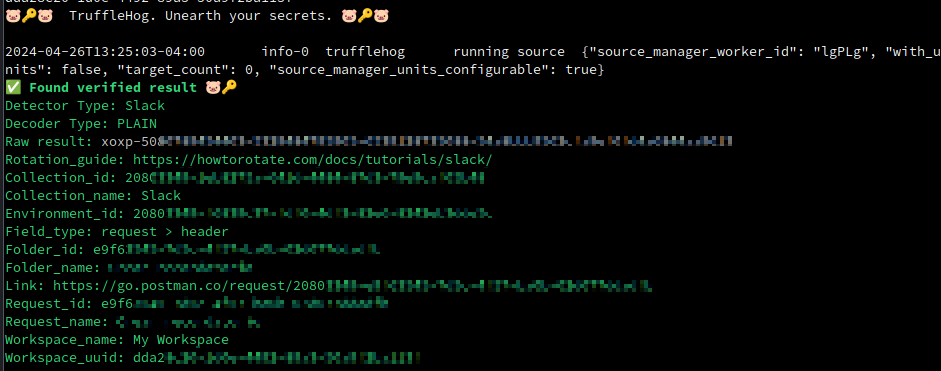
trufflehog –only-verified postman –token “$POSTMAN_TOKEN” –workspace=abcdef-1234-5678-9012-abcdef
With this update to trufflehog, we can also search entire workspaces in a more efficient way.
Resources